HIPAA Compliance Checklist & Guide: What Every Health Tech Team Must Know in 2025
HIPAA protects patient health data, but who needs to comply, and how? Our updated 2025 guide breaks down PHI basics, rules, common violations, and what to do to stay compliant.

Have you ever wondered how patient information protection actually works? Or why HIPAA compliance is such a big deal?
This guide covers everything you need to know in 2025 — from what counts as Protected Health Information (PHI) to key rules, common violations, and what it takes to stay compliant with evolving regulations and expectations.
What Is HIPAA?
HIPAA stands for the Health Insurance Portability and Accountability Act. The Act was introduced on August 21, 1996, and provides national standards for the safety and privacy of Protected Health Information (PHI).
The Office for Civil Rights (OCR) enforces HIPAA, while the Department of Health and Human Services (HHS) manages the regulation of compliance.
What Is Protected Health Information (PHI)?
PHI refers to any demographic or medical data that identifies a patient or client. This includes names, phone numbers, financial data, full facial photos, and more.
When PHI is stored or transmitted electronically, it becomes ePHI — regulated under HIPAA’s Security Rule.
Every HIPAA-responsible organisation is expected to safeguard the integrity, privacy, and security of PHI and ePHI using a structured, compliant approach.

Who Needs to Be HIPAA Compliant?
HIPAA applies to two types of organisations:
- Covered Entities — such as hospitals, laboratories, dentists, optometrists, nurses, mental health providers, radiologists, physicians, pharmacies, call centres, and social workers.
- Business Associates — vendors and third parties who interact with PHI under the authority of a covered entity. This includes IT providers, consultants, accountants, cloud storage companies, and legal or transcription services.
Each party must sign a Business Associate Agreement (BAA) outlining permitted uses of PHI and responsibilities, including secure disposal or return of data.
Enforcement now strongly focuses on vendor risk and cloud misconfiguration — business associates are held equally accountable for HIPAA compliance.
What Are the Main HIPAA Rules?
Since 1996, HIPAA has evolved — notably in 2009 with the HITECH Act (introducing breach rules and digital health incentives), and again during the COVID-19 pandemic, when some flexibilities were temporarily introduced.
The core rules remain unchanged:
1. The HIPAA Privacy Rule
Protects the rights of individuals over their PHI and governs how that information may be used or disclosed. Patients have the right to access and request changes to their data.

2. The HIPAA Security Rule
Applies specifically to ePHI. It requires administrative, technical, and physical safeguards to prevent unauthorised access or disclosure.
3. The HIPAA Breach Notification Rule
Requires organisations to notify affected individuals, HHS, and (for large breaches) the media when PHI is compromised.
4. The HIPAA Omnibus Rule
Clarifies that business associates are also liable for HIPAA compliance. It strengthens patient rights, limits marketing uses, and prohibits the sale of PHI without consent.
Current focus: The OCR has increased scrutiny of unauthorised data sharing, particularly around marketing, telehealth, and AI usage in patient platforms.
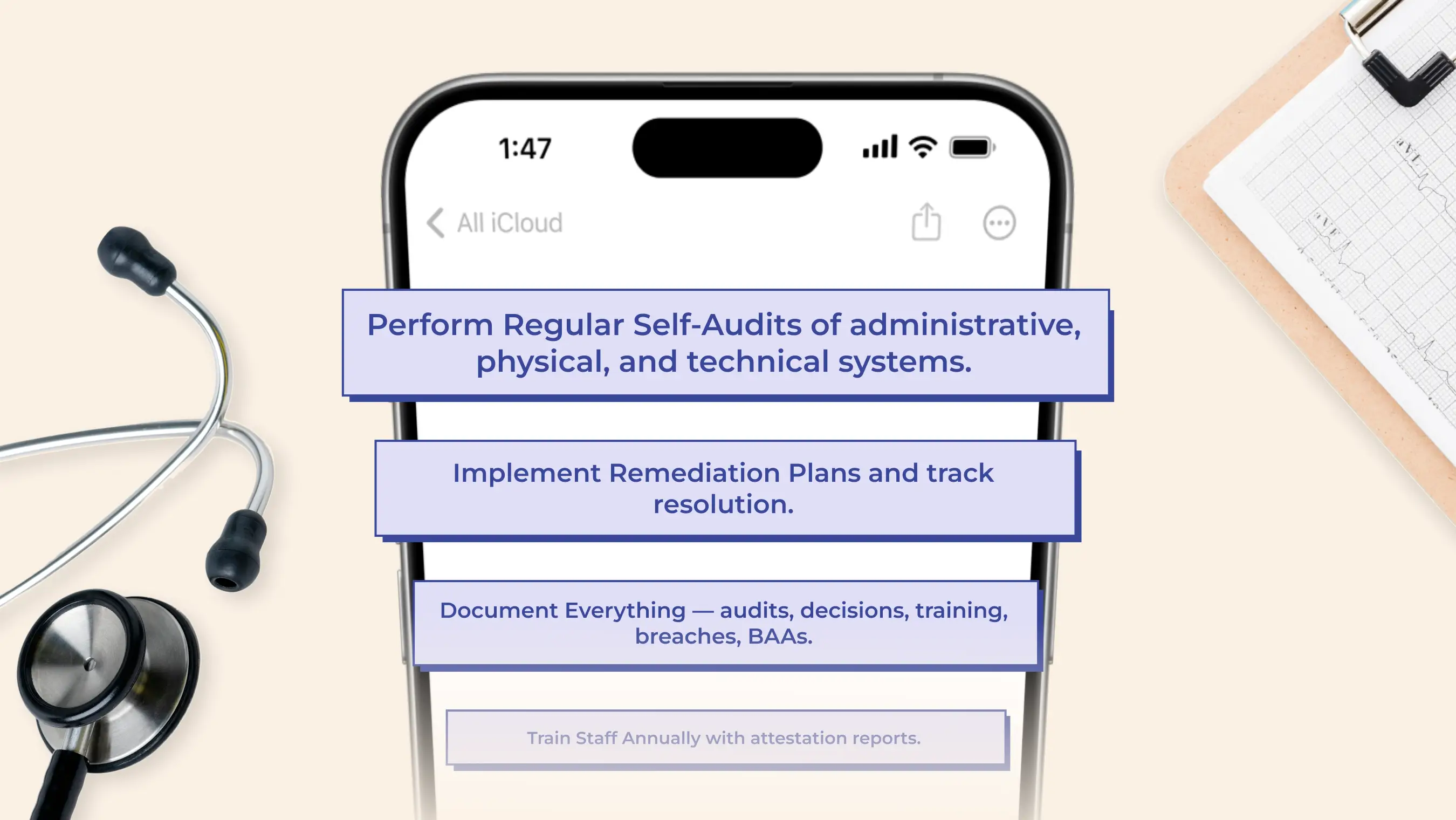
What Is Required for HIPAA Compliance?
To remain compliant, every HIPAA-responsible organisation must:
Common HIPAA Violations
PHI can be worth up to $250 per record on the black market, making data breaches highly costly. Fines for violations can reach $1.5 million per year.
Common causes include:
- Ransomware and hacking
- Sending PHI to the wrong person
- Unencrypted devices (e.g. stolen laptops or phones)
- Sharing PHI on social media
- Cloud misconfigurations
- Third-party vendor failures
The most frequent issues now involve cloud-based environments, poor role-based access controls, and insufficient monitoring of external partners.

HIPAA Compliance Checklist
Administrative Safeguards
- Appoint a HIPAA Officer
- Conduct required audits and document findings
- Provide and record regular staff training
- Keep up-to-date BAAs with all vendors
Physical Safeguards
- Restrict access to physical systems storing ePHI
- Use ID cards, cameras, secure areas
- Maintain disaster recovery and continuity plans
Technical Safeguards
- Encrypt ePHI at rest and in transit
- Enforce access control and auto-logoff
- Monitor access logs and investigate anomalies
Privacy & Breach Notification
- Provide a Notice of Privacy Practices
- Train staff to identify and respond to breaches
- Log and report all data breaches, as required
Omnibus Rule Requirements
- Update policies for new patient rights
- Revise BAAs to reflect the most recent rule changes
- Prohibit unauthorised marketing use of PHI
Don’t forget: Zero Trust and continuous monitoring are now industry best practices for 2025. Traditional perimeter security is no longer enough.
COVID-19 & Post-Pandemic Updates
During COVID-19, the OCR introduced enforcement discretion for remote healthcare solutions. As of late 2023, most of those flexibilities have expired.
Now, full HIPAA compliance is required for:
- Telehealth platforms
- Remote patient monitoring tools
- Digital consultation software
Tips From Our Healthcare Tech Team
- Use layered log-in protection and monitor all levels of access
- Lock out users after repeated failed attempts
- Continuously check login controls
- Closely manage your vendors and BAAs
- Review logs and audit trails frequently
How Diversido Supports HIPAA Compliance
At Diversido, we’ve helped healthcare clients build and launch secure, compliant mobile and web apps from MVPs to FDA-cleared solutions.
Whether it’s a gamified wellness app or a remote learning platform for clinicians, we build with regulations like HIPAA, GDPR, and NHS standards in mind.
Featured apps include:
- Health & Wellness: Bodies Done Right, Visual Gains
- Education: eTutorCloud, Diversido LMS
- On-demand Services: WizFix, Kiwi
- Entertainment & Games: Insiders, Legend of Tapatan
FAQ
Here are the questions most commonly asked by Diversido clients regarding HIPAA.
Does HIPAA apply outside the United States?
No. HIPAA only applies to organisations operating in the U.S. and handling Protected Health Information (PHI) for American patients. If you handle patient data from the EU or UK, you’ll need to comply with GDPR or the UK’s Data Protection Act instead.
What counts as a HIPAA violation?
Any unauthorised use, access, or disclosure of PHI. That includes emailing records to the wrong person, lost or stolen devices with unencrypted data, unauthorised third-party access, or improper sharing on social media.
Are cloud-based apps HIPAA-compliant by default?
No. Compliance depends on how you configure and manage the cloud service. You'll need encryption, access controls, audit logging, and a signed Business Associate Agreement (BAA) with the cloud provider.
We use third-party tools — are we still responsible?
Yes. Even if a vendor processes PHI, your organisation is responsible for ensuring their compliance. You must have a valid BAA and verify their safeguards regularly.
What are the penalties for non-compliance?
Fines range from $100 to $50,000 per violation, with an annual maximum of $1.5 million. Penalties can apply even if no harm was done, especially for lack of proper safeguards or documentation.
What if a patient requests access to their data?
You must provide access within 30 days (under the Privacy Rule). You can charge only a reasonable, cost-based fee. Denying access without proper cause is a common source of complaints.
Is there a deadline for compliance?
HIPAA is ongoing. There’s no one-time certification. Compliance is about continuous risk management, documentation, and staff training.
Do we need legal or technical experts to be compliant?
You don’t need in-house lawyers, but you do need experts who understand healthcare, security, and the legal framework. That’s why many companies partner with HIPAA-experienced development teams like Diversido.
Need help building a HIPAA-compliant app? Let’s talk!


.png)